Last week I was in London at the InfoSecurity convention having a look what is happening in the security world. If you have never attended InfoSecurity, it is a free event where most of the presentations are a bit loaded on the marketing side. Of course there are always exceptions. The 2-hour workshops are truly gems. At least the workshops which I did attend to.
What if you could protect VM’s without agents or without any other piece of installed software?
The workshop which really caught my attention was the workshop presented by Andrei IONESCU and Adrian Liviu ARSENE who are both employed by Bitdefender: ‘Data Center Security – HYPERVISOR INTROSPECTION’. Starting with explaining how external and internal threats are evolving they quickly moved on to explain how their top tier product Gravity Zone SVE -which by the way can be integrated with NSX- deals with these evolving threats. However it was the second part of their presentation which really caught my attention.
Direct Inspect API and Hyper Visor Introspection
Agentless Hypervisor based protection! Wait agentless, does that exist!? Don’t we always need at least a light agent or a module such as the VMCI driver which is provided by VMware Tools and which is used for guest introspection integration in case you use NSX and a compatible AV solution? The answer is a bit of yes and a bit of no. Yes, because Bitdefender has found a way to use an API to inspect the live host memory instead of scanning the memory in the guest OS. Unfortunately it is also a bit of no because at the time of this writing, Bitdefender only supports true agentless protection on Xen server.
A bleak future for Direct Inspect API and Hyper Visor Introspection?
In the near future Bitdefender will offer the same agentless solution for KVM virtualization but
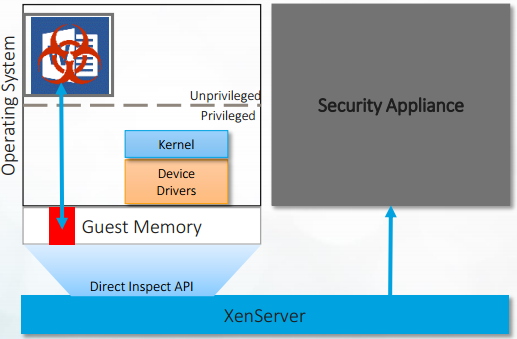
How Agentless protection works on Xen server
Although you now know that there is no agentless solution yet for vSphere, I still want to give you an overview of how it works, because it is truly a very interesting concept and I think this concept is elegant in its simplicity.
Threats are blocked by blocking the backdoors at the system level, not at the guest OS level. This makes sure that the threat cannot be executed in the Guest OS itself. Just think about it, when a threat gets in the Guest OS, the agent might be compromised as well. So you need to stop the attack technique before it gets a foothold into the guest OS.
So how does Hyper Visor Introspection accomplish this? Bitdefender has an API which can be deployed on the Hyper Visor. HVI leverages the Bitdefender Direct inspect API’s in the Hyper Visor which allows HVI to trap and inspect operations which are not permitted.
This looks wonderful, but how does HVI actually do this? HVI actually uses hardware to make sure it is running at a higher level of privilege than the malware which runs in the guest OS and because of that it is able to inspect and clean the threat from the host memory before it reaches the guest OS. See the picture below.
So in a nutshell:
A threat is detected by the Bitdefender security appliance, which through the API in the host, is scanning the Hypervisor’s memory. Next the Bitdefender security appliance will automatically remove the threat before it can be exploited in the VM which the threat was supposed to compromise.
 Discovery!
Discovery!
 Automatic clean up!
Automatic clean up!
Why I am that excited about this
It is not just about the potential increase in security to me. Obviously, if this agentless solution will work well on all virtualization platforms, it will be a true godsend.
But also think about this from an operational perspective: When you have to take care of thousands of VMs, upgrading VMware Tools and agents in all of these VM’s is not always the operation you like best. Although it is technically very easy to upgrade VMware Tools and agents, let’s be honest here, when you run enterprise class datacenters the reboot needed to complete the upgrade of tools and agents is not always desired: There are the additional operational costs to consider, reboots have to fall in the maintenance windows, in some cases T1 and T2 applications have to be failed over before upgrading tools and agents in the guest OS, you need official approval from the line managers, business units and stakeholders and then you need to figure out how to do all that without creating a negative non-signed off impact on the business. For sure it is doable, we have all done this, but it can be a lot to coordinate and it comes with certain risks. Agentless would make sense in these cases too, not? I know it does make sense to me, a lot of sense. Should I be able to skip operations without compromising the environment in my care, I don’t even have to think about it, agentless it is.
So from my point of view, I really hope VMware and Microsoft will support the Bitdefender agentless solution/vision and I am sure I am not the only one who might want that, am I?
Kim
PS: This isn’t a sponsored article. All drawings are copyrighted by Bitdefender. I have used the pictures after receiving permission from Andrei IONESCU and Adrian Liviu ARSENE.




Leave a Reply